A3S3 - Automated Android Audit of Safety and Security Signals
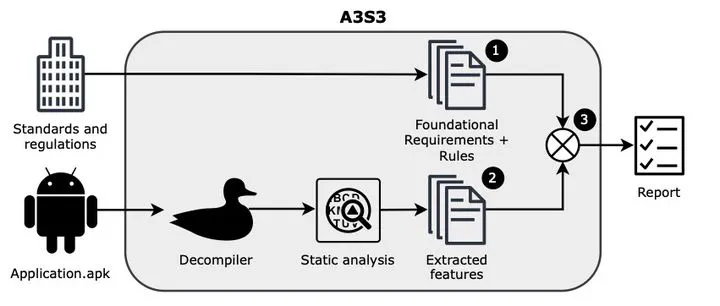 A3S3 conceptual overview
A3S3 conceptual overview
Abstract
Android devices and related applications are increasingly prevalent in our daily routines. Furthermore, these technologies are being used for more than just connecting people around the world. Indeed, Android devices are more and more connected to external sensors or used as sensors, directly gathering data from their environment, which brings them closer to Cyber Physical Systems (CPS). When used for specific purposes such as health, Android devices and related applications can be life-critical (insulin pumps, heart monitoring, etc.), requiring guarantees specific to the application domain. Interestingly, when considering the technical security in domains related to operational technologies, we can see that many standards are available while not directly intended for Android applications. Other regulatory texts can also be valuable to drive an audit process, although they need more effort to reach technically testable requirements from the legal requirements they define. In particular, Android applications are developed using various device permissions (i.e., resource access), external libraries, etc. In this paper, we present A3S3 a tool to link requirements from industry standards and regulatory texts to Android features to drive a security audit. Following research in the cyber-security community, we suggest an approach based on static code analysis of Android applications to retrieve good and bad signals, denoting potential violations, related to non-functional requirements.
Type
Publication
Proceedings of the 2025 International Conference on Advanced Information Systems Engineering (CAiSE)
